Cybersecurity is one of the fastest-growing industries in the world, and one of the hardest to market. Global spending has reached roughly $213 billion in 2025, according to Gartner, as companies race to protect expanding digital infrastructures. Yet, despite rising budgets and constant threat headlines, cybersecurity firms face a different challenge: being noticed in an already crowded market.
Thousands of vendors claim to offer “AI-powered,” “Zero Trust,” or “next-generation” protection. Most sound the same. Buyers, meanwhile, are increasingly skeptical, evaluating vendors through peer networks, analyst reports, and independent reviews long before filling out a form. Visibility alone no longer wins deals; credibility, clarity, and timing do.
The problem isn’t that cybersecurity companies lack solutions. It’s that their messaging rarely matches how today’s buyers discover, compare, and validate them. This article outlines how cybersecurity marketers can adapt: understanding the unique buyer journey, positioning their brands with precision, and using modern visibility strategies to stand out where decisions actually start.
Understanding the Cybersecurity Buyer Journey
Cybersecurity buyers behave differently from typical B2B audiences. Their purchase process is slower, more private, and shaped by risk rather than novelty. Every new tool has to prove it will strengthen defenses without adding complexity or compliance gaps. As a result, the journey is not a smooth funnel but a series of validations where marketing needs to earn attention at each stage.
How It Differs from a Standard B2B Journey
In most B2B categories, discovery is public. Buyers read articles, attend webinars, and interact early with vendors. Cybersecurity buyers, by contrast, operate under caution. CISOs, IT leads, and compliance managers often research anonymously through trusted peers and analyst reports long before engaging with sales. The sensitivity of the topic discourages casual conversations and lengthens sales cycles.
Typical traits:
- Extended evaluation: internal reviews, risk scoring, and controlled pilots.
- Multiple decision-makers: security, IT, finance, and legal all weigh in.
- Higher stakes: failure isn’t a productivity dip, it’s a potential breach.
- Marketing teams need to recognize that visibility isn’t just about reach; it’s about appearing credible in the channels buyers already trust.
Mapping the Cybersecurity Buyer Path
The journey typically follows such checkpoints:
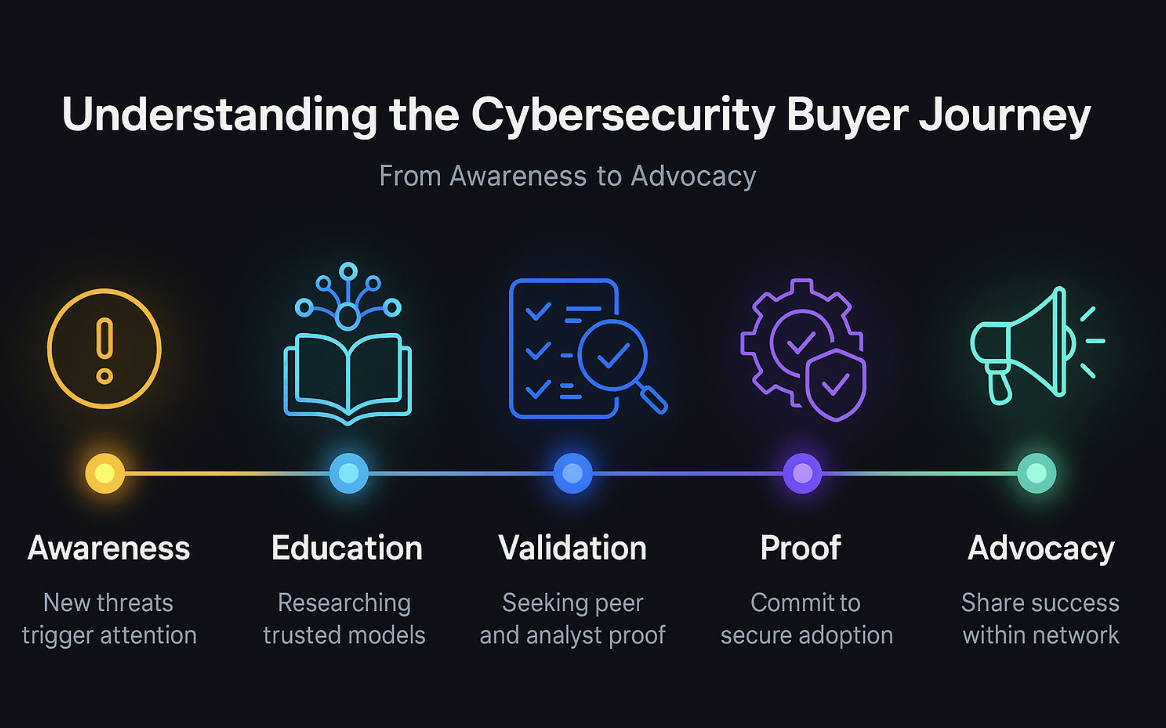
- Awareness: Sparked by new threats, audits, or compliance shifts.
- Education: Buyers explore categories — “AI-powered,” “Zero Trust,” “XDR” — to understand which models apply.
- Validation: They turn to case studies, analyst briefings, and peer forums for evidence.
- Proof: Controlled demos or pilot tests confirm capability and integration.
- Purchase & Advocacy: Once verified, buyers become long-term partners and, later, advocates, one of the few scalable organic channels in this niche.
Understanding this buyer path is essential, and it’s the foundation behind how LenGreo structures marketing strategies that align with real cybersecurity decision cycles.
Core Strategies for Cybersecurity Marketing in 2026
Understanding how cybersecurity buyers think is one part of the equation. The next step is turning that insight into strategies that make your brand visible and credible in a market overflowing with similar claims. Cybersecurity marketing in 2026 will reward brands that align precision with proof. The following strategies focus on visibility, differentiation, and measurable growth, all built around how cybersecurity buyers now discover and decide.
Position Your Brand with Clarity, Not Complexity
Cybersecurity audiences are flooded with jargon. Every vendor claims to be “AI-powered,” “Zero Trust,” or “next generation.” These terms still matter but only when backed by meaning. Strong positioning connects a specific problem with a verifiable outcome, not a buzzword.
To stand out:
- Define the one or two outcomes you deliver better than anyone else: faster detection, simpler integration, or lower response costs.
- Translate technical language into business value. Instead of “adaptive endpoint telemetry,” say “real-time visibility that cuts incident response time.”
- Demonstrate how your solution integrates with the existing security stack, rather than replacing it.
- Maintain a confident tone, not an inflated one: clarity is what builds authority in this space.
Positioning is where most cybersecurity brands lose buyers early. Those who explain what changes for the client — not just what powers the product — are the ones that stay remembered.
Build Visibility Across SEO, AEO, and GEO
Cybersecurity keywords are among the most competitive in digital marketing. Ranking for “endpoint protection” or “cloud security platform” is nearly impossible without specialization. The solution is a layered visibility strategy that meets buyers where they search, in both traditional and AI-driven environments.
- SEO: Focus on intent-based, specific queries. Content that answers “how to comply with SOC 2” or “what is incident response automation” attracts higher-quality traffic than generic product pages.
- AEO (Answer Engine Optimization): Structure FAQs, glossaries, and concise expert explainers, so AI tools like Google’s AI Overviews or Bing Copilot can quote them accurately.
- GEO (Generative Engine Optimization): Produce authoritative, data-backed content that AI summarizers (like Perplexity or ChatGPT search) are more likely to surface.
Cybersecurity buyers value proof and precision. Optimizing your content for credibility, with clear authorship, factual accuracy, and external validation, strengthens performance across all three search layers.
Generate Demand Efficiently
Paid ads remain essential but inefficient if handled traditionally. Cybersecurity CPCs are high, and many search platforms restrict security-related ads. Instead of chasing volume, shift toward precision and context.
- Use LinkedIn and niche media (Dark Reading, VentureBeat, The Hacker News) to reach decision-makers in relevant discussions.
- Replace product-heavy ads with insight-led offers: “Cloud Threat Playbook,” “SOC Efficiency Benchmark,” or “Zero Trust Implementation Checklist.”
- Run retargeting campaigns around educational content rather than homepages to catch buyers mid-journey.
- Combine paid reach with partner channels, such as integrations, webinars, and co-authored research pieces, as they often convert faster than cold ads.
The goal is to position your brand where trust already exists, within ecosystems that cybersecurity buyers consult.
Leverage Earned Media & Partnerships
With ad reach limited and buyers cautious, credibility now spreads fastest through earned visibility and trusted alliances. Media coverage and partner collaborations extend awareness more effectively than pure promotion.
- Earned media: Expert commentary, research contributions, or interviews in respected outlets validate authority.
- Press releases: Share news that matters (product milestones, research, or partnerships) supported by clear data.
- Collaborative campaigns: Joint webinars, co-branded reports, or integrations widen reach and borrow trust.
- Partner ecosystems: Visibility within MSSPs, GSIs, or cloud marketplaces connects you directly with active buyers.
Consistent presence in credible spaces turns awareness into reputation, a lasting advantage in a market where trust sells faster than ads.
Measure What Actually Moves Deals
Traditional marketing KPIs don’t capture how cybersecurity buyers behave. High click rates mean little if the audience is unqualified or still in research mode.
Meaningful metrics include:
- High-intent leads: demo requests, proof-of-concept signups, or event participation.
- Engagement depth: average read time on technical explainers or downloads of compliance assets.
- AI visibility: frequency of brand mentions or citations in AI-generated summaries and answer boxes.
- Pipeline velocity: time from first inquiry to signed contract, a strong proxy for message clarity.
For cybersecurity companies, success is less about volume and more about relevance. Measuring the right signals ensures marketing resources support both visibility and revenue.
Together, these strategies create a marketing framework that matches how cybersecurity decisions are truly made — cautiously, collaboratively, and through trusted information channels. They turn awareness into credibility and credibility into demand.
Overcoming Industry Barriers to Cybersecurity Growth
Even with rising budgets and global awareness, cybersecurity companies face some of the toughest marketing conditions of any B2B field. The obstacles are not just about competition, they stem from the structure of the industry itself. Recognizing these barriers is essential before any strategy can gain traction.
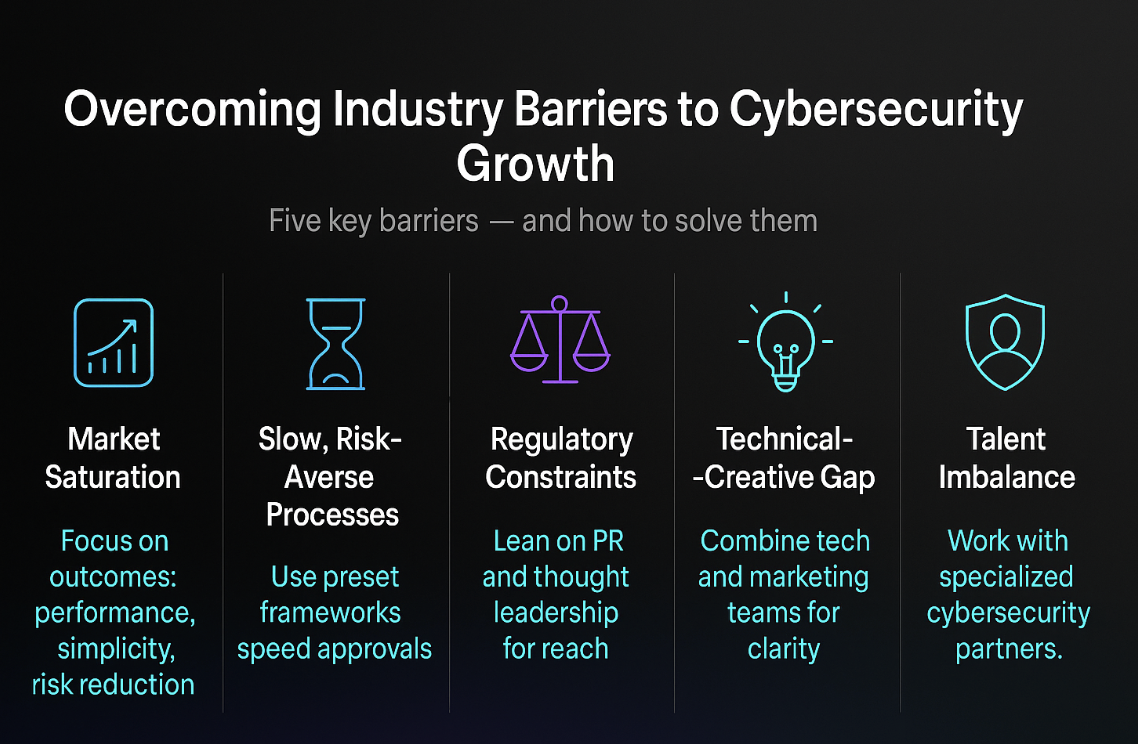
- Market Saturation and Message Fatigue
The cybersecurity market has become saturated with similar claims. Every platform promises “AI-powered protection” or “next-generation security,” and most buyers have stopped listening. This sameness makes differentiation difficult even for strong products.
*Marketing teams need to focus on what actually changes for the client — performance, simplicity, or measurable risk reduction — rather than repeating feature lists. Clear, specific language breaks through where abstract claims don’t.
- Slow, Risk-Averse Processes
Because cybersecurity communication touches sensitive topics, internal review cycles are notoriously slow. Legal and compliance teams often take weeks to approve a single campaign. This lag not only limits agility but also prevents timely responses to new threats or trends.
*Companies that create predefined approval frameworks and reusable templates shorten this cycle dramatically. Fast communication is a competitive advantage in a field where relevance fades quickly.
- Regulatory and Advertising Constraints
Privacy and data laws make digital advertising harder for cybersecurity vendors than for most other industries. Many keywords are restricted or come with higher scrutiny, while ad platforms apply additional filters to security-related terms. As a result, visibility through paid search alone rarely scales.
*Earned media, PR coverage, and thought-leadership collaborations are proving more reliable ways to reach audiences that distrust direct promotion.
- The Technical–Creative Gap
Another persistent barrier is the divide between engineers and marketers. Security products are complex, and explaining them in a way that resonates with business decision-makers is difficult. Marketing teams without technical fluency struggle to simplify concepts without losing meaning, while technical experts often over-explain.
*Cross-functional collaboration (writers working directly with engineers or product leads) helps translate expertise into language that drives adoption.
- Talent and Resource Imbalance
Demand for cybersecurity marketing talent has grown faster than supply. Few professionals combine industry knowledge, compliance awareness, and digital strategy skills. Many companies try to train internal teams, but progress is slow.
*Partnering with specialized agencies or consultants who already understand the field’s vocabulary, buyer mindset, and regulatory nuances can fill that gap efficiently.
Overcoming these barriers requires operational discipline as much as creative skill. Cybersecurity brands that fix structural issues (approval speed, clarity of message, and adaptability) position themselves to make every strategic effort that follows more effective.
Conclusion
There’s no single blueprint for marketing cybersecurity solutions. Each company faces a different mix of audience maturity, product complexity, and regulatory limits; this means the best strategy is always the one built around those realities. What works for a managed detection provider won’t work the same for a compliance platform or a data-privacy startup.
Still, the principles hold: clarity over jargon, relevance over reach, and credibility earned through proof, not claims. Marketing in this space succeeds when it mirrors how cybersecurity decisions actually unfold: cautious, evidence-based, and peer-influenced. The brands that stay consistent across these stages are the ones buyers remember when the time to act comes.
LenGreo helps cybersecurity companies shape strategies that reflect that complexity, aligning clear messaging, search visibility, and demand generation with the way buyers truly research and decide. Because in cybersecurity, there’s no one-size-fits-all approach — but there is a right way to be found.










